Trust Mechanisms to Secure Routing in Wireless Sensor Networks: Current State of the Research and Open Research Issues

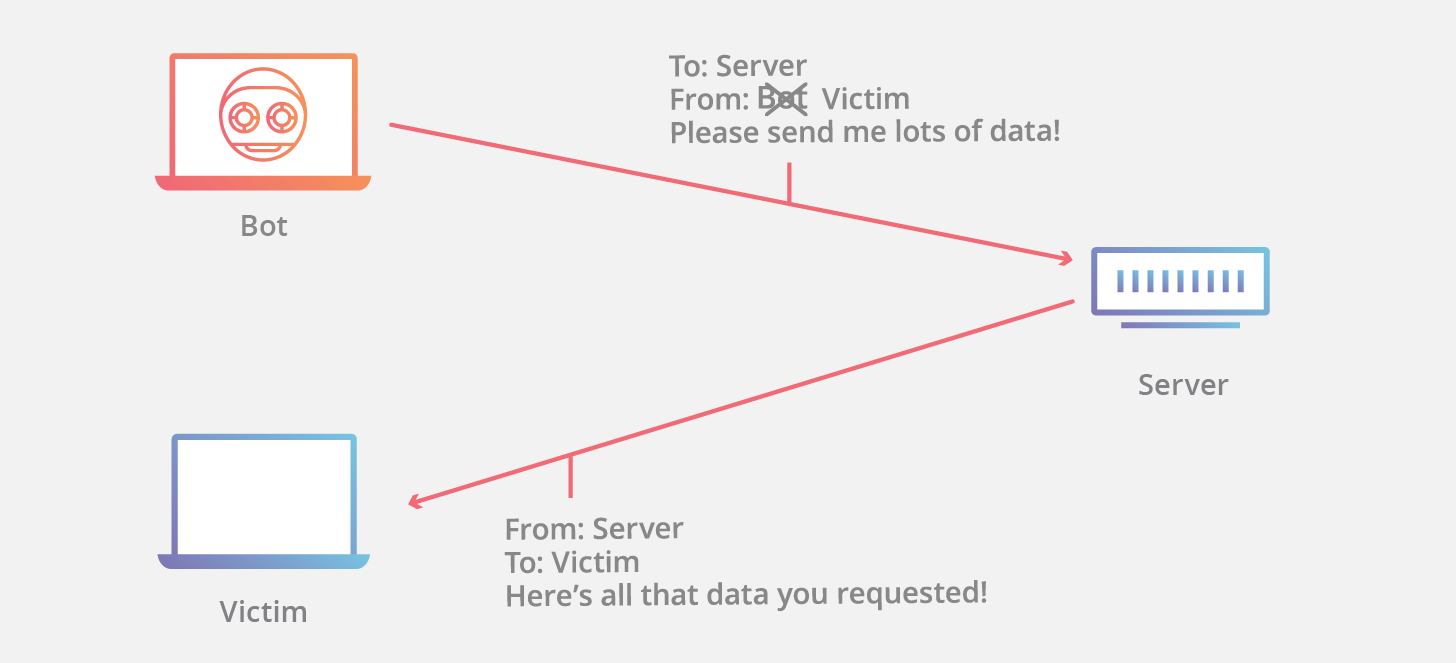
How to Help Protect Dynamic Web Applications Against DDoS Attacks by Using Amazon CloudFront and Amazon Route 53 | AWS Security Blog

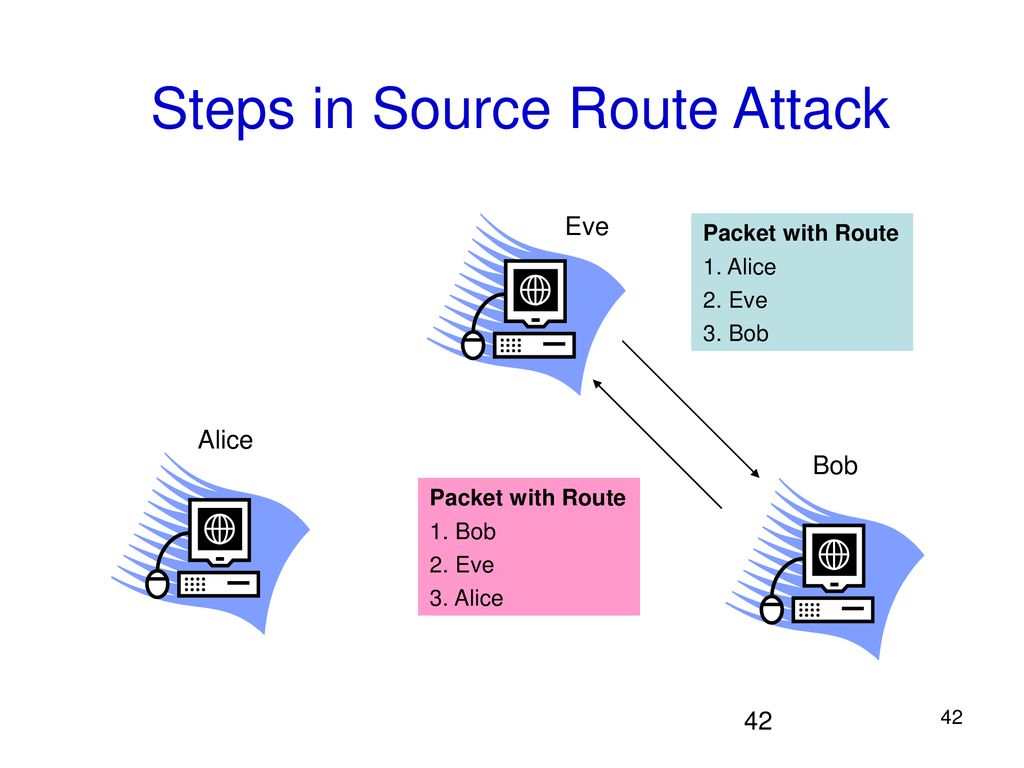
Malicious route construction attacks on source routing: stretch attack | Download Scientific Diagram

Malicious route construction attacks on source routing: stretch attack | Download Scientific Diagram

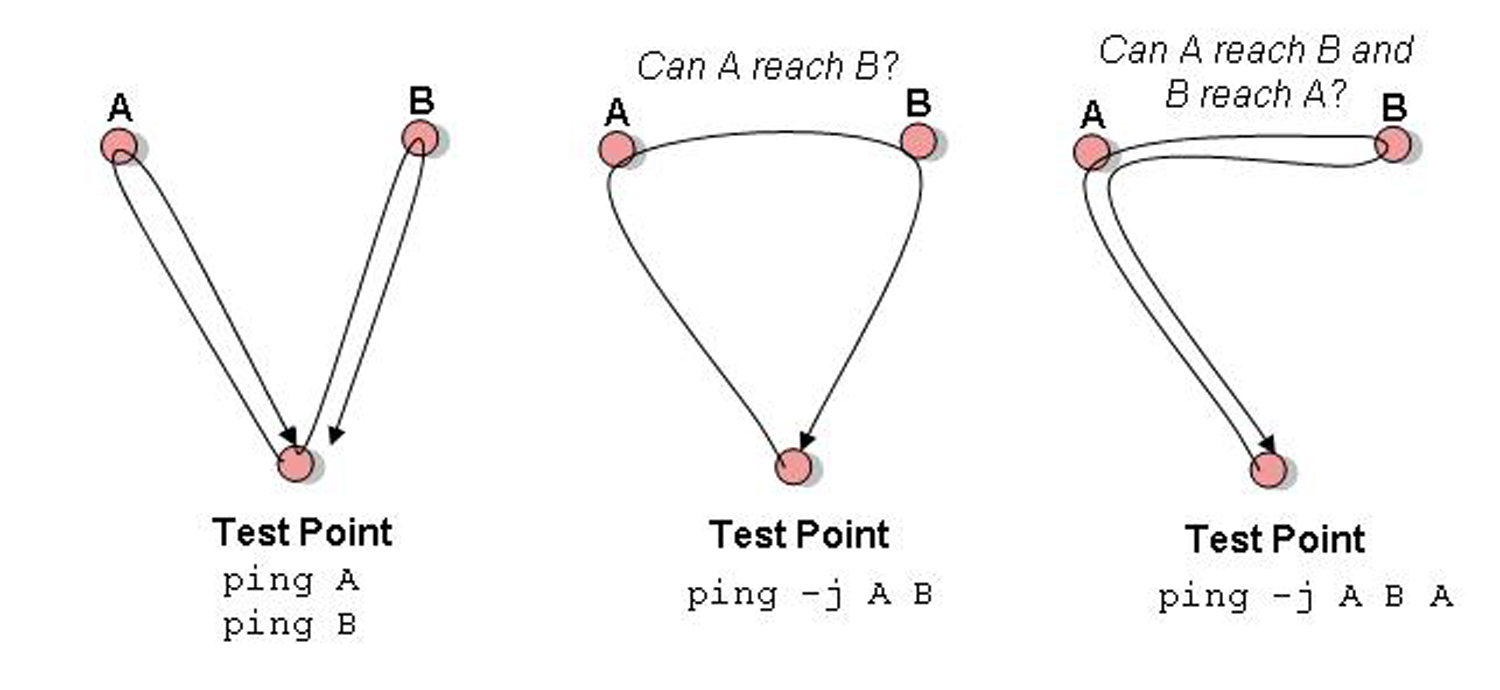
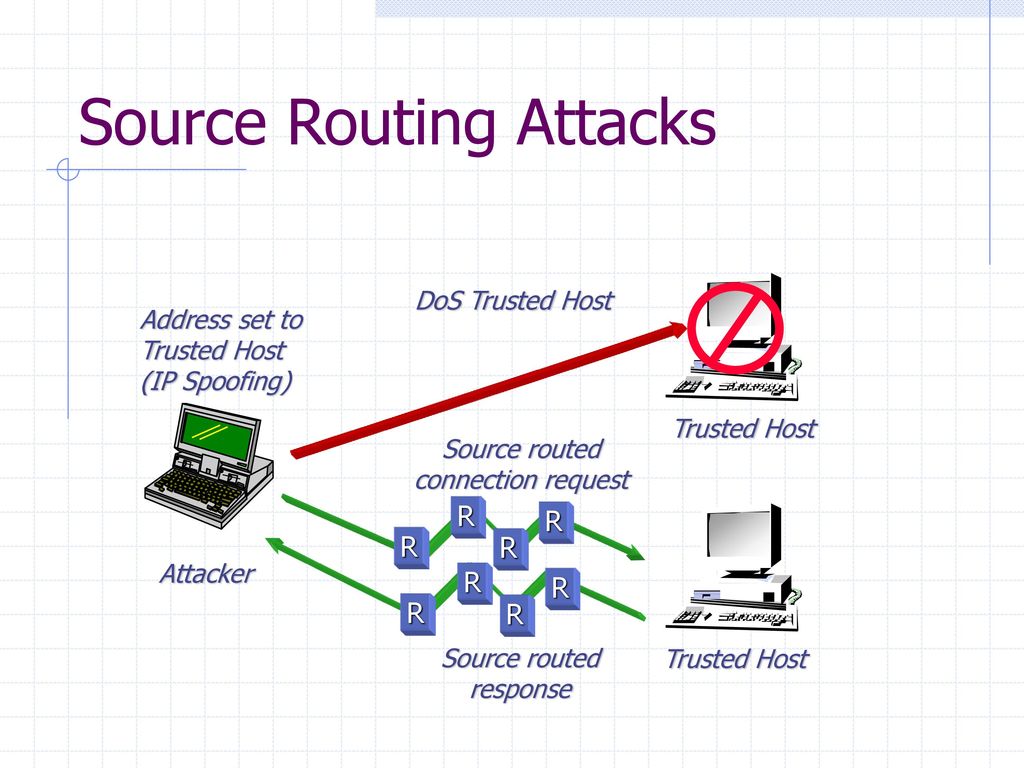
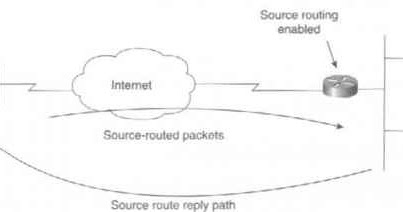
Cisco Certifications - Short & Quick. for CCENT/CCNA candidates. Why is it regarded as good practice to disable IP source routing on your infrastructure routers? #attack #networksecurity #misconfiguredIP Ryan at Cisco

Malicious route construction attacks on source routing: carousel attack | Download Scientific Diagram