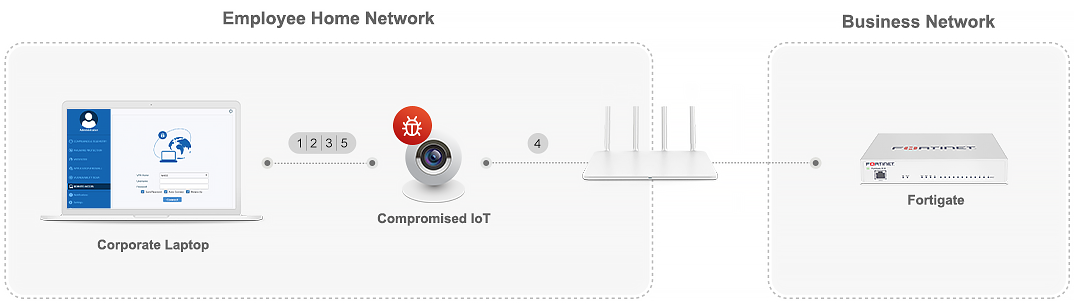
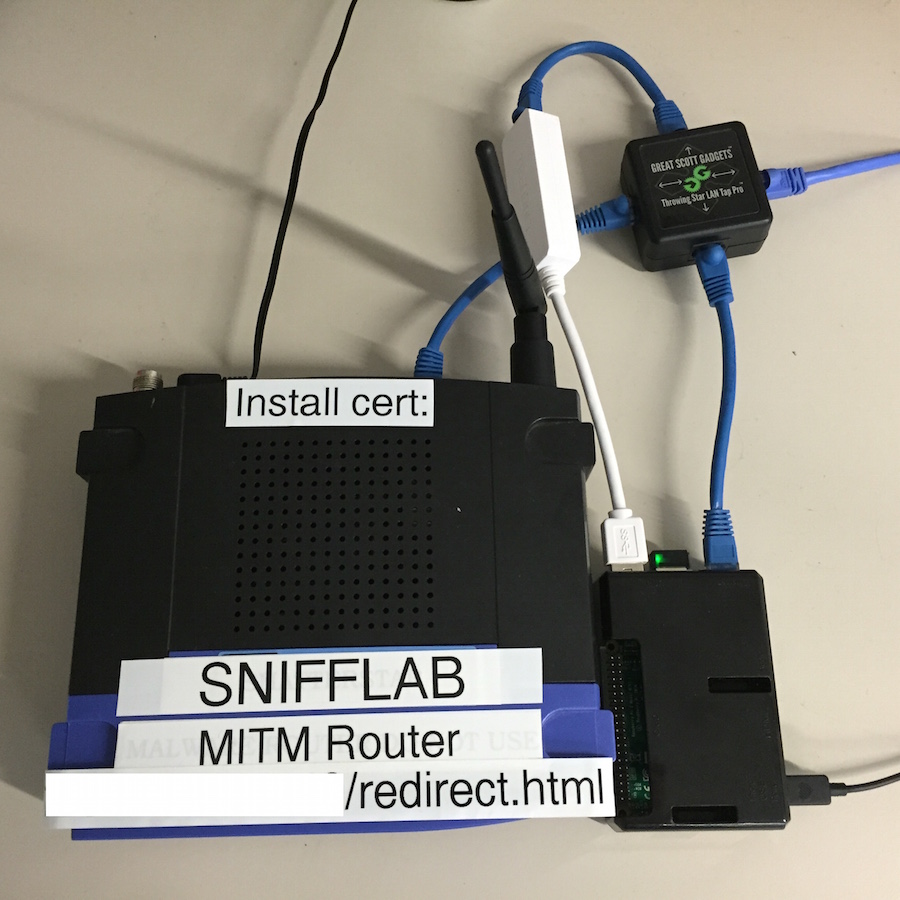
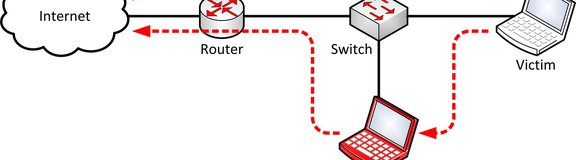
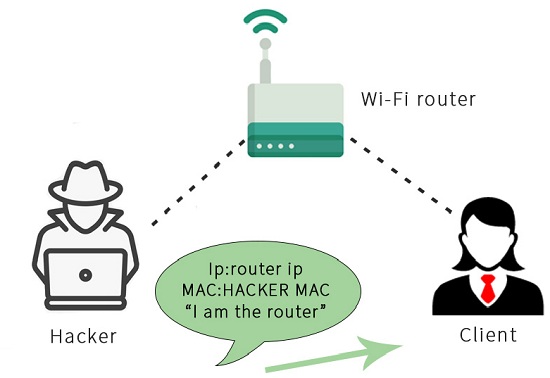
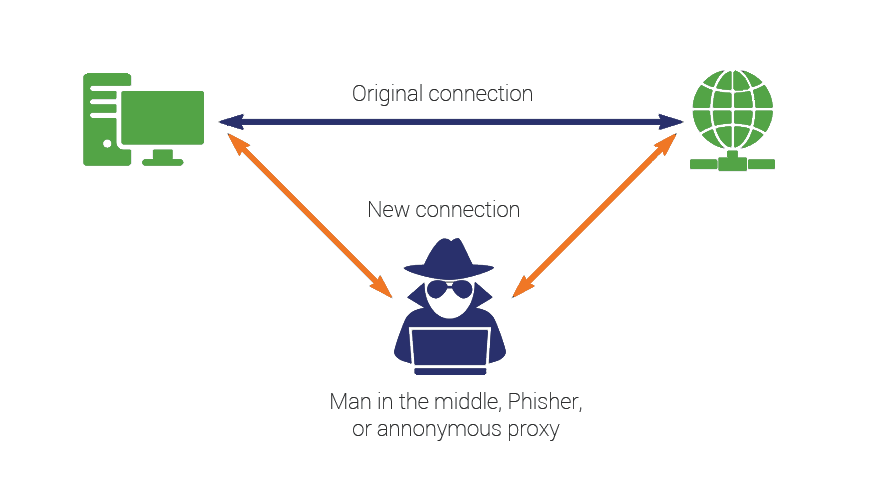
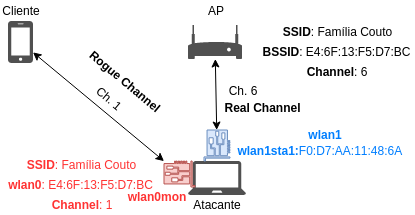
A man in the middle (MITM) attack is a general term for when a perpetrator positions himself in a conversation between a user and an… | Router, Tutorial, Networking

Cara Melakukan Penyadapan Dengan Teknik Main In The Middle Attack (MITM) | Informasi Seputar Pengetahuan