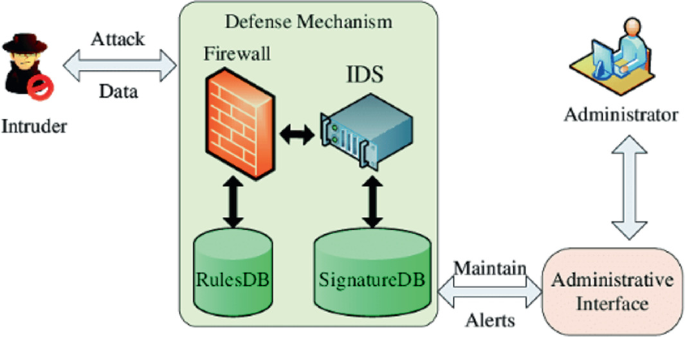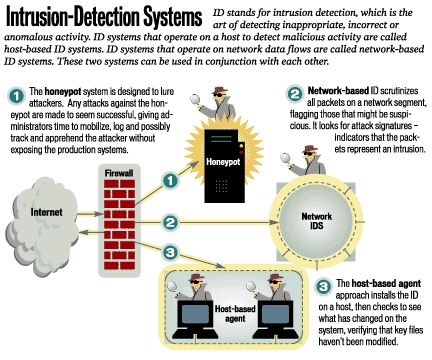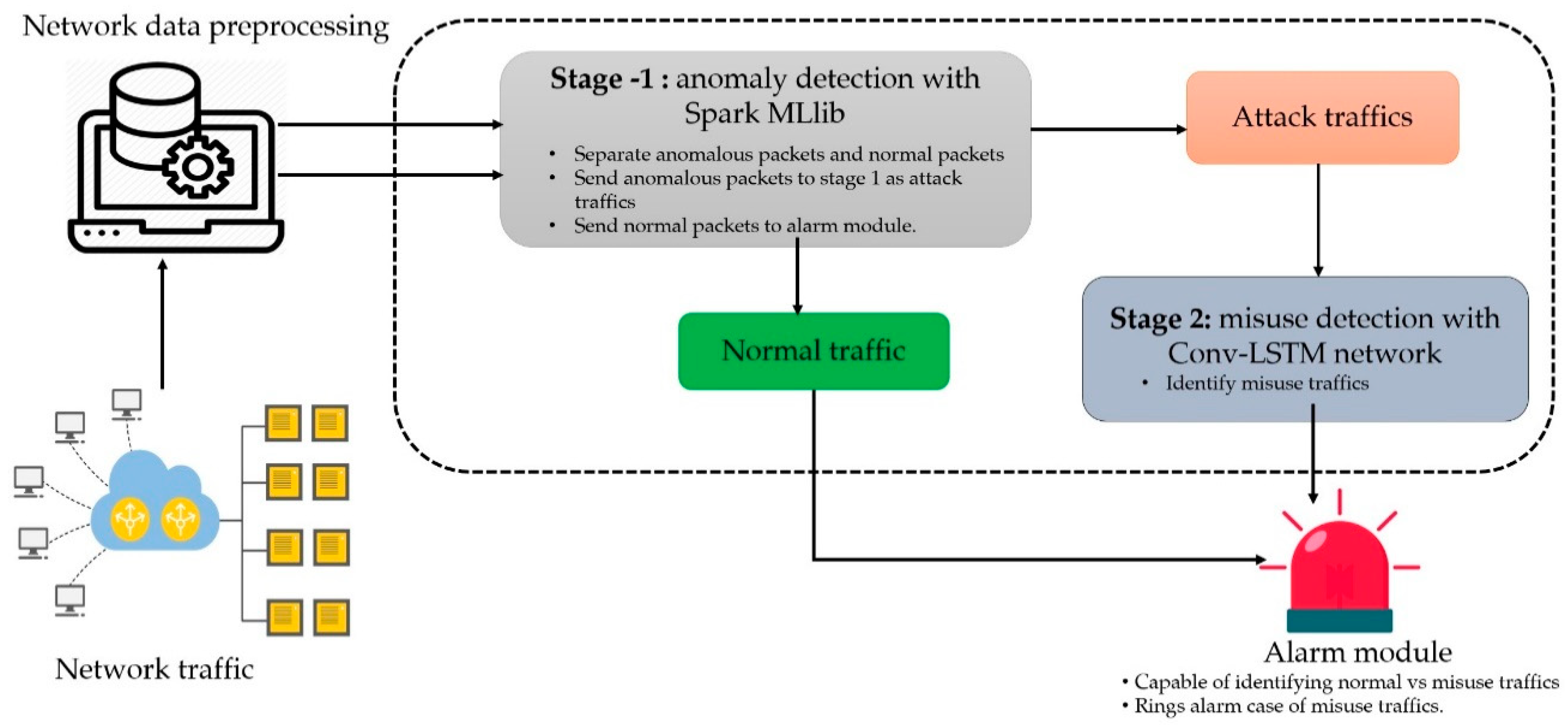
Symmetry | Free Full-Text | A Scalable and Hybrid Intrusion Detection System Based on the Convolutional-LSTM Network

An improved malicious code intrusion detection method based on target tree for space information network - Chundong She, Yaqi Ma, Jingchao Wang, Luting Jia, 2017
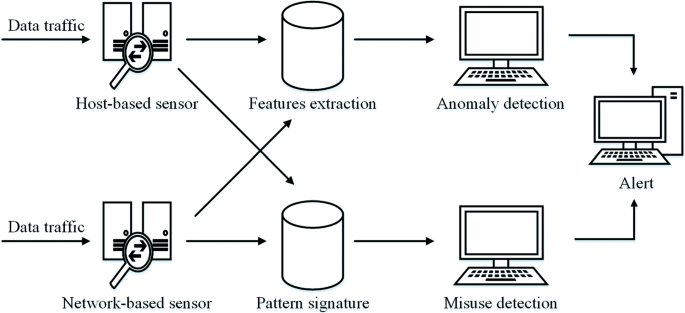
Intrusion detection systems for IoT-based smart environments: a survey | Journal of Cloud Computing | Full Text
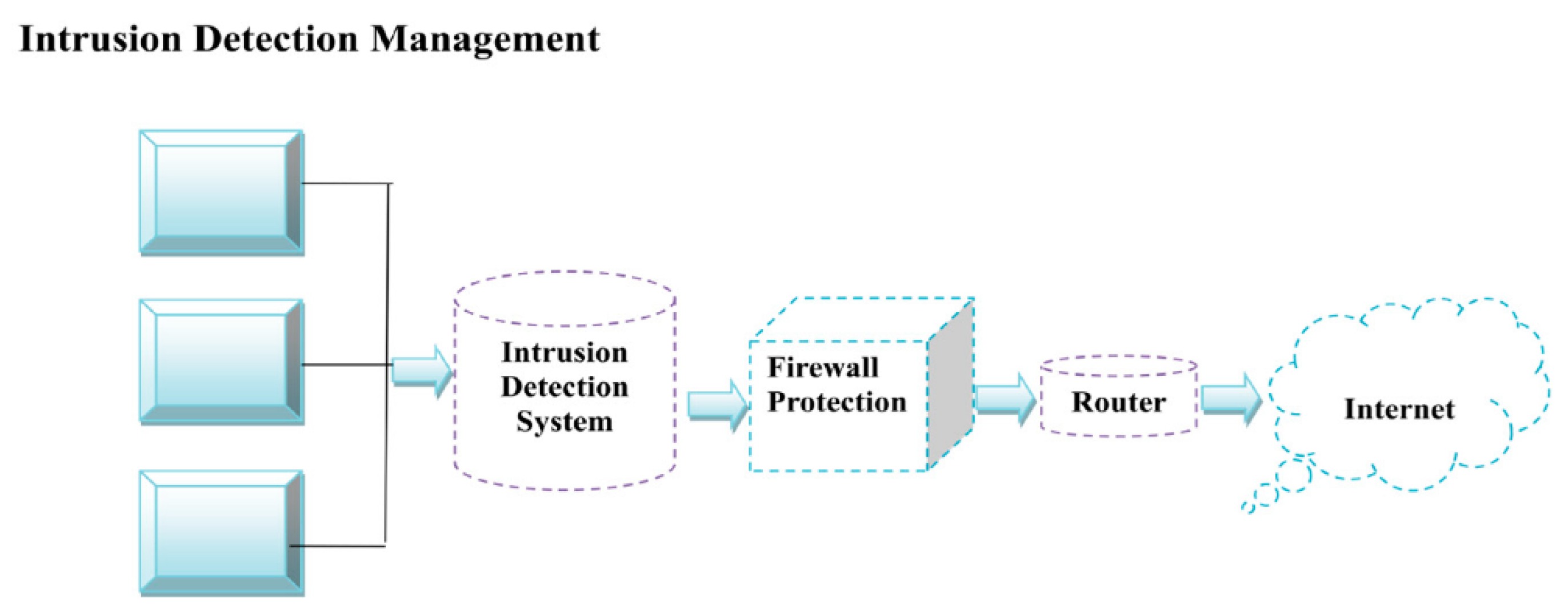
Sensors | Free Full-Text | A Hybrid Intrusion Detection Model Using EGA-PSO and Improved Random Forest Method
![PDF] Intrusion Detection in the Era of IoT: Building Trust via Traffic Filtering and Sampling | Semantic Scholar PDF] Intrusion Detection in the Era of IoT: Building Trust via Traffic Filtering and Sampling | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e3bdfd5a2fd2672dacfd34a5e402b68b9283e16f/3-Figure2-1.png)
PDF] Intrusion Detection in the Era of IoT: Building Trust via Traffic Filtering and Sampling | Semantic Scholar
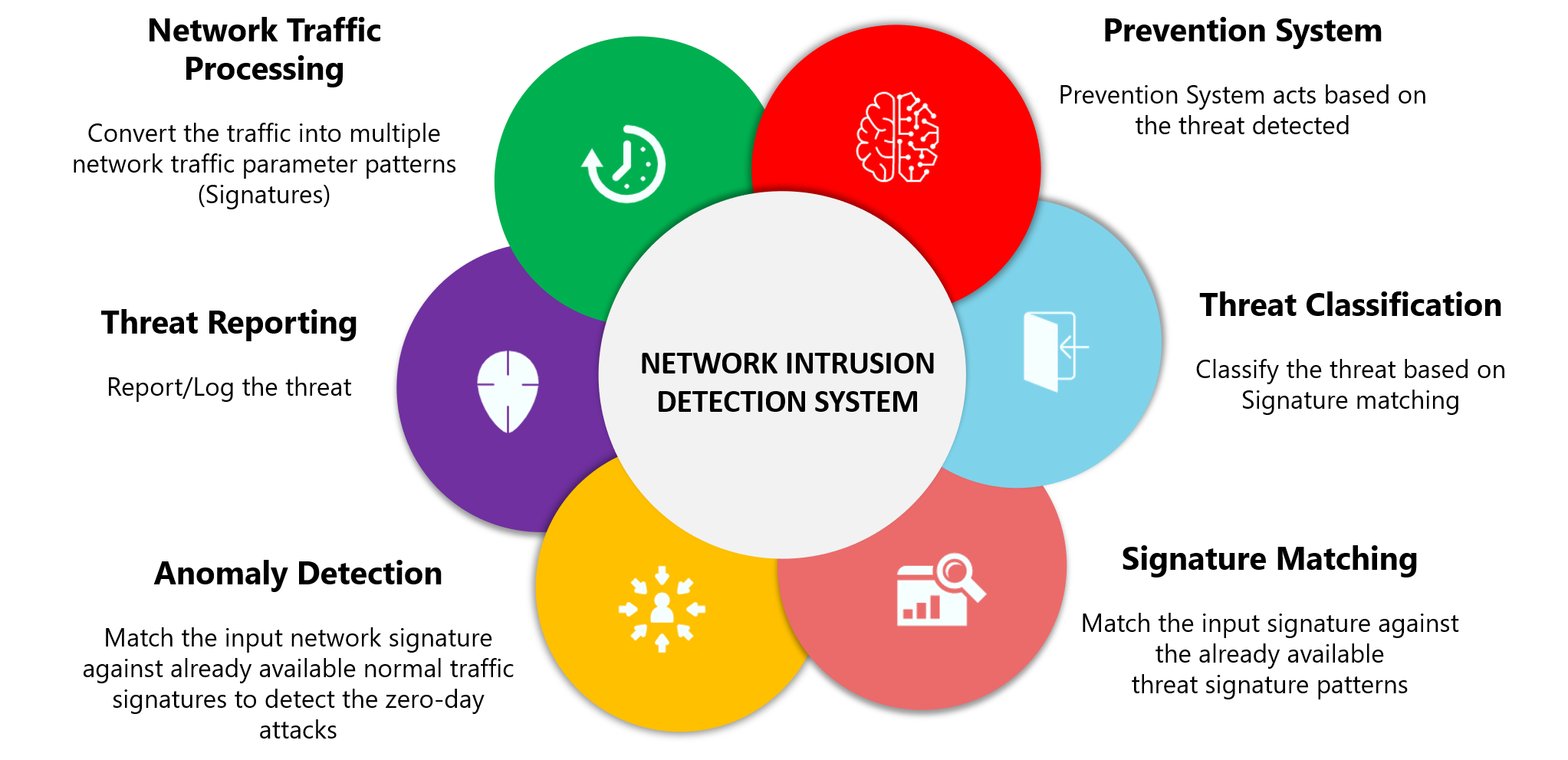
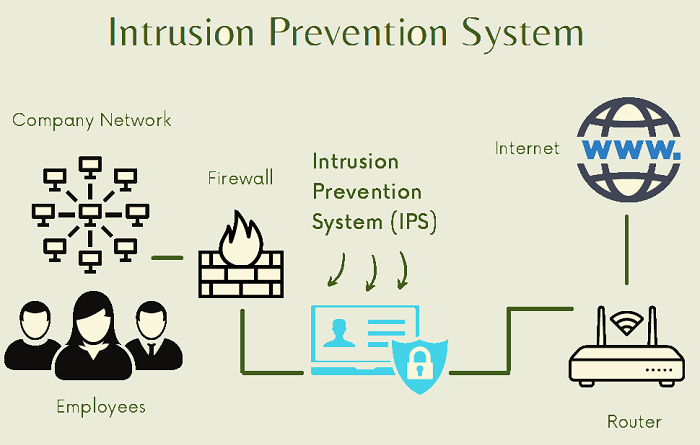
Securing the Internet of Things with Intrusion Detection Systems - BPI - The destination for everything process related
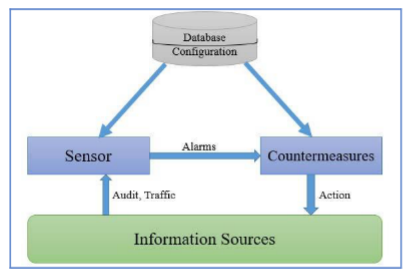
A Robust Intrusion Detection Mechanism in Wireless Sensor Networks Against Well-Armed Attackers | International Journal of Intelligent Systems and Applications in Engineering
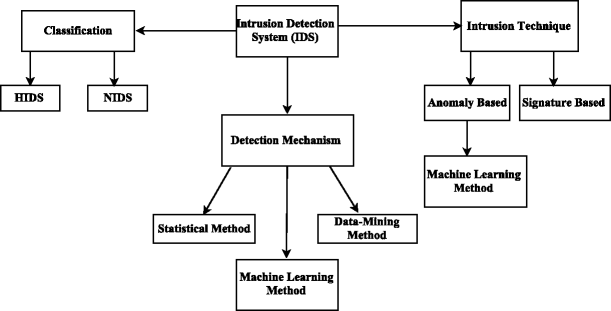
Survey on SDN based network intrusion detection system using machine learning approaches | SpringerLink

Network intrusion detection system: A systematic study of machine learning and deep learning approaches - Ahmad - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
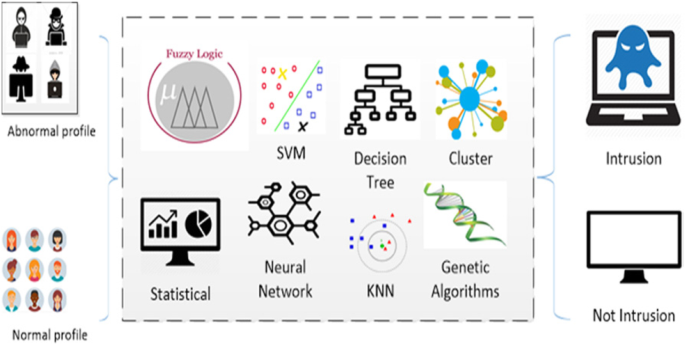
Survey of intrusion detection systems: techniques, datasets and challenges | Cybersecurity | Full Text
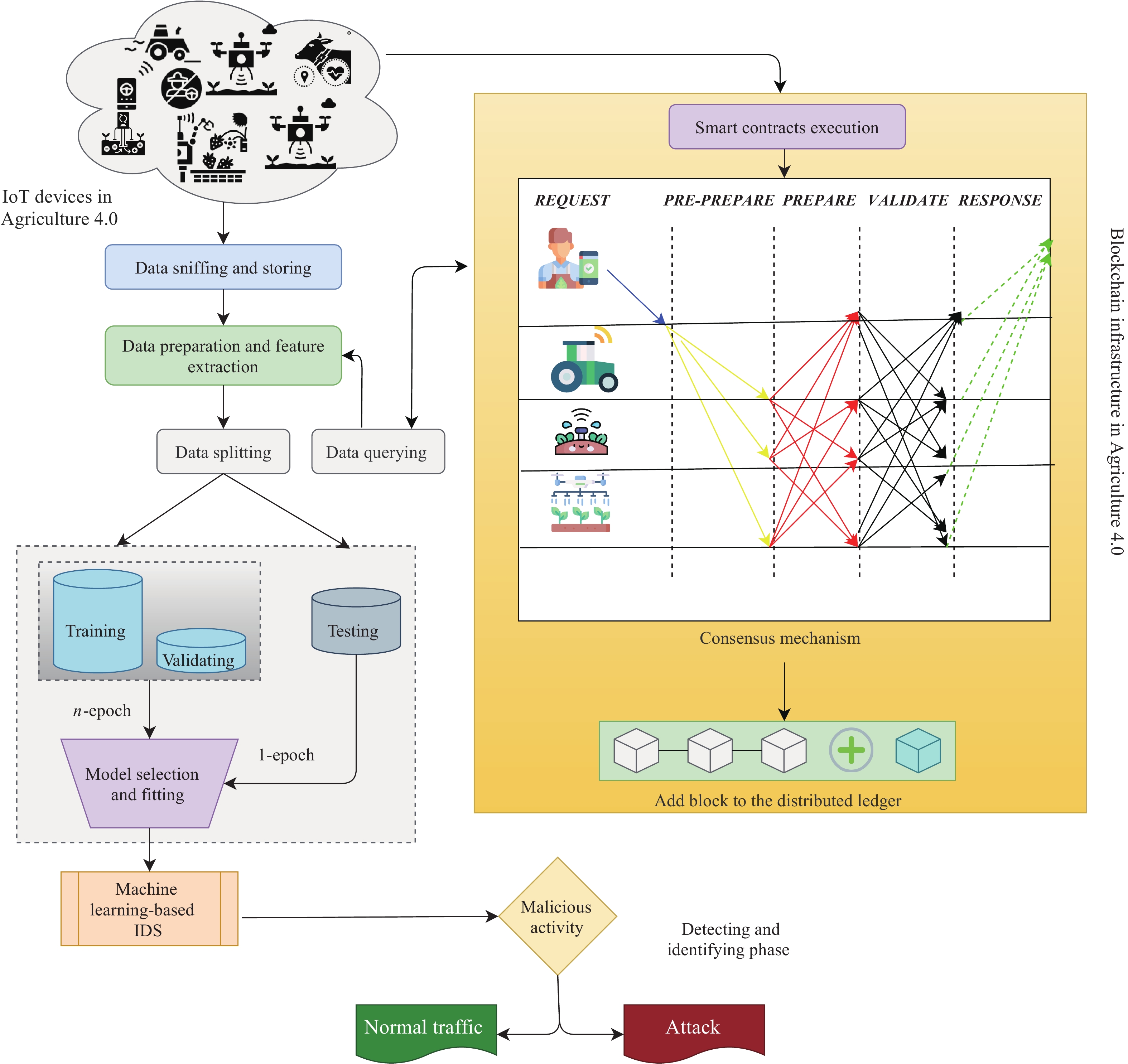
![Network intrusion detection using oversampling technique and machine learning algorithms [PeerJ] Network intrusion detection using oversampling technique and machine learning algorithms [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-820/1/fig-1-2x.jpg)




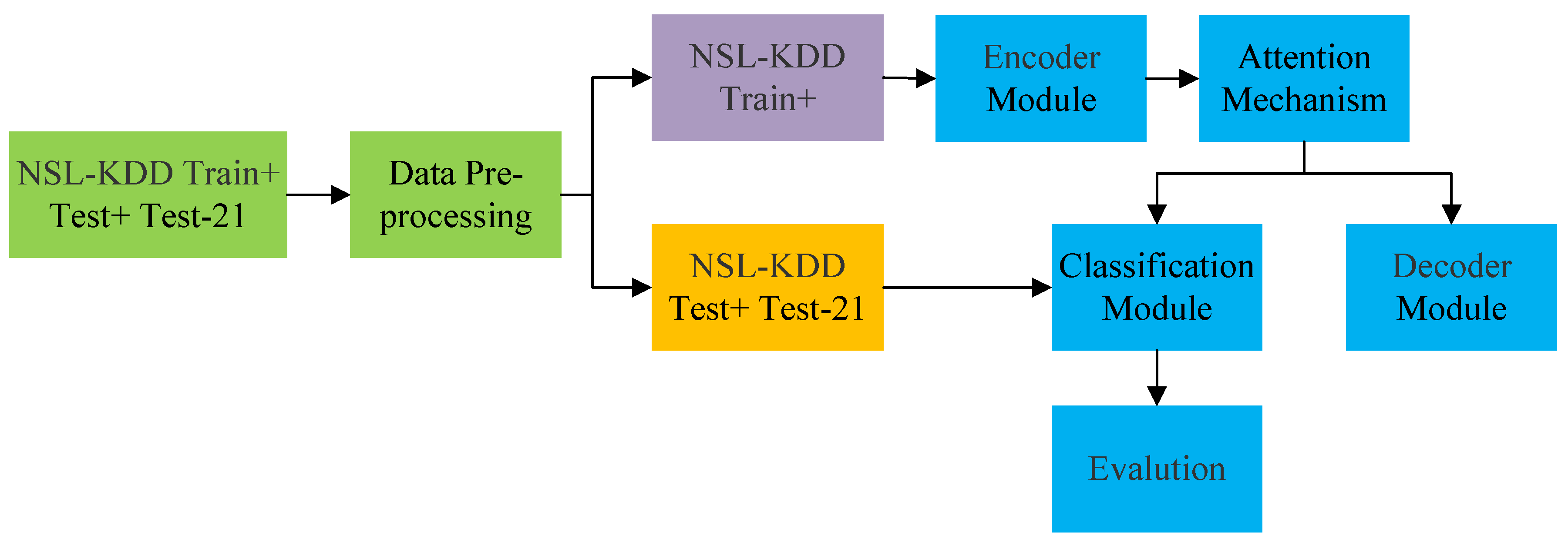


![PDF] Intrusion Detection Systems, Issues, Challenges, and Needs | Semantic Scholar PDF] Intrusion Detection Systems, Issues, Challenges, and Needs | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6612eb4f569736d1ddb0e93b815a55f8ac815133/2-Figure1-1.png)